Blockchain provided new definitions for the use of decentralization in data storage, transfer, and efficient execution of financial transactions. It offers a distributed ledger or database with abilities to store public and private transactions or digital assets. The blockchain records every transaction on the ledger, followed by agreement among the different participants in the system. You could identify answers for ‘what is consensus algorithm’ in the fundamental way of working of blockchain. Consensus algorithms help in ensuring that all the distributed nodes within the decentralized network have agreed on the status of specific records of transactions and related data. Consensus is an important requirement for ensuring the reliability of the network and agreement among participants on specific transactions. However, consensus algorithm issues have become one of the prominent concerns for blockchain and Web3 projects. The following post offers you a detailed overview of some of the notable challenges for consensus algorithm security.
Build your identity as a certified blockchain expert with 101 Blockchains’ Blockchain Certifications designed to provide enhanced career prospects.
What is Consensus Algorithm?
Before you learn about the challenges associated with consensus algorithms and their security issues, you must familiarize yourself with their definition. What is the importance of consensus algorithm in blockchain and the related application? Blockchain technology has been tailored to create a decentralized, immutable, and distributed ledger.
Every node in the blockchain network has the capability to maintain copies of the ledger. On top of it, every node must also update their copy of the ledger after verification of new blocks. The decentralized aspect of blockchain nodes helps in improving resilience alongside implementing a trustless system.
The answers to “What is consensus algorithm” explain how they are crucial for validating the official version of every block in a blockchain network. Consensus algorithms play a vital role in defining who would validate and create the next block in the blockchain. As a result, they can avoid disputes among conflicting variations of a blockchain while ensuring decentralization.
The importance of consensus algorithm security is closely related to the security of the overall blockchain network. Nodes that can control the block creation process can also exert control over the historical records associated with blockchain networks.
Goals of Consensus in Blockchain
Learners interested in identifying the challenges and security issues with consensus algorithms must know the primary objectives of consensus algorithms. You can find out why consensus algorithms must be fault tolerant by learning about the goals of consensus in the blockchain. The goals of consensus can help you identify its significance in the working of blockchain. First of all, consensus, as the name implies, helps in ensuring that all participants on a blockchain network agree to the validity of certain transactions.
The next significant value advantage of consensus is the advantage of aligning the economic incentives for participants with the growth of blockchain protocols. Interestingly, the responses to “What is consensus in security?” would reflect on the ways in which consensus mechanisms reward good behavior and impose penalties on malicious actions. Another important highlight among the goals of consensus algorithms points to ensuring fair and equitable access to blockchain networks and related protocols.
The basic functions of consensus algorithms also include the facility for preventing double-spending. Consensus mechanisms ensure that only valid and verified transactions are added to the public blockchain. The objectives of consensus algorithms also include fault-tolerant governance, which ensures accessibility to the system regardless of threats.
Start learning Blockchain with World’s first Blockchain Skill Paths with quality resources tailored by industry experts Now!
Most Notable Consensus Algorithms
The basic explanation of consensus mechanism fundamentals alongside their goals proves their importance in the blockchain landscape. Now, you need to review every consensus algorithm example for a better understanding of the potential challenges associated with them. You can find two distinct types of consensus algorithms, such as proof-based and voting-based consensus algorithms.
Proof-based algorithms focus on nodes performing computation for generating proof to earn the right to mine new blocks on the chain in return for rewards. On the other hand, voting-based consensus algorithms focus on the participation of selected verifiers in the validation and addition of new blocks. Here is an outline of the popular consensus algorithms you would come across in the world of blockchain.
Please include attribution to 101blockchains.com with this graphic. <a href='https://101blockchains.com/blockchain-infographics/'> <img src='https://nftsteacher.com/wp-content/uploads/sites/15/2023/05/Popular-consensus-algorithms.png' alt='Popular consensus algorithms='0' /> </a>
-
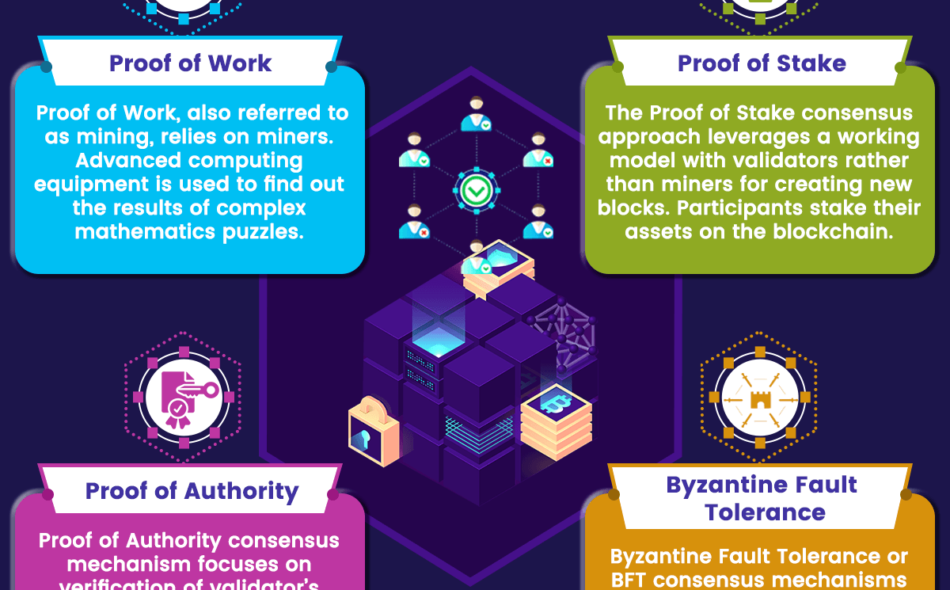
Proof of Work
Proof of Work is the earliest consensus mechanism developed by Satoshi Nakamoto for the Bitcoin blockchain. The working of Proof of Work, also referred to as mining, relies on miners. Participating nodes in the network have to use advanced computing equipment to find out the results of complex mathematics puzzles.
Proof of Work ensures limited consensus algorithm issues, owing to the need for expensive equipment and efforts for breaking down the network. Proof of Work has gradually become one of the popular consensus mechanisms adopted across healthcare, business management, and governance.
Want to become a bitcoin expert? Enroll Now in Getting Started with Bitcoin Technology Course
-
Proof of Stake
The big alternative to Proof of Work is the Proof of Stake algorithm. It is one of the common examples you would find in response to ‘What is consensus algorithm’ and offers viable improvements over Proof of Work consensus. For example, Proof of Stake provides better environmental sustainability in comparison to Proof of Work.
The Proof of Stake consensus approach leverages a working model with validators rather than miners for creating new blocks. Participants who wish to participate in the consensus can stake their assets on the blockchain. The network would randomly select validators for specific transactions and would receive a share of the transaction fees upon successful validation. On the contrary, bad actors can lose their stake in negative behavior, which affects network integrity.
-
Proof of Authority
Another notable addition among the top choices of consensus algorithms in blockchain refers to Proof of Authority. It is an improvement over the Proof of Stake consensus mechanism and focuses on the verification of the validator’s identity. In the Proof of Authority consensus mechanism, validators have to put their reputation at stake. The nodes which earn the authority for validation could only create new blocks, and validators receive incentives for putting their identity at risk.
-
Byzantine Fault Tolerance
The next popular choice among consensus algorithms in blockchain refers to Byzantine Fault Tolerance or BFT consensus mechanisms. You can learn how consensus algorithms must be fault tolerant to avoid disruptions when the network has some dubious participants. The two most common types of BFT consensus algorithms include the Practical Byzantine Fault Tolerance or PBFT consensus and Delegated Byzantine Fault Tolerance or DBFT.
Many other consensus algorithms have emerged in the blockchain landscape with crucial value-based advantages. Why do you need so many consensus algorithms when Bitcoin works on Proof of Work? You need to notice how every new consensus algorithm wants to be better than its predecessor. Therefore, it is reasonable to conclude that consensus algorithms have setbacks alongside their multiple advantages.
Curious to learn about blockchain implementation and strategies? Enroll Now in Blockchain Technology – Implementation And Strategy Course!
Challenges and Security Issues for Popular Consensus Algorithms
The discussions on challenges and security issues with consensus algorithms focus on the two commonly used consensus algorithms. You can find better answers to “What is consensus in security?” by identifying how consensus among network participants is vital for safeguarding blockchain protocols. Interestingly, a careful overview of the Proof of Work and Proof of Stake algorithms, alongside their challenges, can help in the identification of security issues.
-
Challenges in Proof of Work Consensus
The original consensus mechanism Proof of Work presented the beauty of consensus algorithms to the world. Proof of Work relies on computing power as a scarce resource, and miners have to compete against each other to find the exact hash required to create the new block. However, the consensus algorithm example of Proof of Work shows that possession of more computation resources can offer an advantage to a specific node.
Therefore, control over computing power would directly relate to the control over Proof of Work blockchains. The in-built vulnerability with Proof of Work consensus can allow attackers to take complete control of a blockchain network by gaining control over a major portion of the computational resources of the network.
Interestingly, Proof of Work consensus algorithms has a viable solution to such problems. Blockchain networks with a large number of high-end computing resources and equipment can make it difficult for hackers to acquire the majority of the network resources. Therefore, attackers might come up with new consensus algorithm issues to compromise the security of Proof of Work consensus mechanisms.
For example, attackers can go for selfish mining attacks in which the attackers create one blockchain on top of another. The lack of information about the previous block creates issues in generating the next block. Selfish miners do not reveal the blocks immediately after discovering them, thereby gaining an unfair advantage over other miners.
Another security issue with the Proof of Stake consensus mechanism refers to SPV mining. In the Proof of Work consensus mechanism, the miners have to ensure that every transaction in the block is free of any conflicts with previous blocks. Attackers can use SPV mining to create a block that contains the transaction for paying block rewards and use it repeatedly for extracting unauthorized rewards.
-
Challenges for Proof of Stake Consensus
The claims for introducing fault tolerance in consensus algorithms would also involve an overview of the challenges for Proof of Stake consensus. It is reasonable to assume that consensus algorithms must be fault tolerant for secure operations. However, the involvement of multiple validators and the need for staking crypto assets creates prominent challenges for Proof of Stake consensus.
For example, the chances of selection of validators depend on their stake in the network. What about the other participants with lesser stakes in the network? As a matter of fact, the design of Proof of Stake presents an in-built vulnerability. Attackers can gain control over the network by controlling more than half of the stakes in the protocol.
The most prominent mention among issues pertaining to the security of consensus algorithms in the blockchain would refer to the 51% attack. Attackers with control over the majority of the staked resources could gain control over the network. The next challenge for the Proof of Stake blockchain refers to the possibility of a long-range attack.
Long-range attacks involve the creation of competing versions of a blockchain, and they create new blocks when they are selected as validators. Gradually, attackers can gain control over the stake in their blockchain and ensure its faster growth in comparison to the parent blockchain.
Start your blockchain journey Now with the Enterprise Blockchains Fundamentals – Free Course!
Conclusion
The problems with consensus algorithms emerge from basic faults in the design. It is important to understand that consensus algorithm issues can challenge the long-term adoption of blockchain-based solutions. In most cases, blockchain consensus algorithms follow the principle of ensuring security through scarcity. The control over scarce resources can define power over the creation of blocks and expansion of the blockchain network.
Scarce resources can establish controlling power on blockchain networks and ensure safety against malicious actors on the network. However, attackers can use such aspects to gain control over the network and its security. Therefore, it is important to learn about consensus algorithms and their design and work to avoid critical issues in the functioning of blockchain networks, systems, and applications. Learn more about consensus algorithms and the basics of blockchain technology in detail right now.
*Disclaimer: The article should not be taken as, and is not intended to provide any investment advice. Claims made in this article do not constitute investment advice and should not be taken as such. 101 Blockchains shall not be responsible for any loss sustained by any person who relies on this article. Do your own research!
The post Challenges and Security issues in Consensus Algorithm appeared first on 101 Blockchains.