Decentralized technologies and blockchain-based platforms have emerged as popular trends in the domain of technology. Does blockchain serve a transformative impact only in the form of cryptocurrencies and NFTs? The working of blockchain has created the foundations of web3, a new version of the internet. Web3, dApps, and smart contracts are leading the world toward a revolutionary future where users would have control over their data and online experiences.
At the same time, security in web3 has also emerged as a formidable topic as users have to encounter different types of security threats in web3. The problem with web3 is that you cannot rely on the inherent security principles of web3. For example, the transparency of smart contracts on public blockchains can expose different types of vulnerabilities to malicious agents.
Web3 serves as a decentralized version of the web with a peer-to-peer network, where users won’t need intermediaries such as social media companies, tech giants, and banks. One of the foremost highlights in a web3 security guide would point at the fundamental security principles associated with web3.
The security principles in web3 include cryptography, which facilitates encryption and security for data. Similarly, blockchain technology provides a secure ledger for web3 transactions through immutability. Let us learn more about web3 security and best practices for safeguarding your digital assets.
Importance of Safeguarding Digital Assets in Web3
Before seeking insights about best practices for web3 security, you must learn about the importance of safeguarding your digital assets. The traditional scope of cybersecurity revolved around securing digital assets such as files and folders that did not store anything of monetary value. If a security solution can safeguard users from downloading malicious software or clicking on suspicious websites, then it is considered a reliable tool for cybersecurity.
However, web3 has changed the definition of digital assets with the arrival of cryptocurrencies and NFTs. Users can rely on blockchain-based decentralized platforms for owning, storing, and controlling digital assets, including cryptocurrencies and NFTs. In a way, web3 turned the internet into a safe deposit box that allows creation, storage, and exchange of assets with monetary value.
The decentralized version of the internet introduced new variants of security risks. Users must learn web3 security principles and best practices to avoid their valuable assets from theft. It is important to remember that web3 removes intermediaries, and the responsibility of safeguarding digital assets falls on the users. Therefore, it is important to understand how web3 security differs from web2 cybersecurity.
Learn the fundamentals, challenges and use cases of Web3.0 blockchain from Introduction To Web3 E-Book
Differences between Web2 and Web3 Security
When you compare web2 with web3 in terms of security, you will find that web2 security breaches are temporary, and users can solve them easily. On the other hand, web3 security risks are likely to have massive consequences for users. For example, security breaches in web2 can lead to loss of information, such as names, credit card numbers, or addresses. Such types of attacks can lead to exposure to sensitive information on the internet. However, credit card companies could take responsive action by freezing the cards and issuing new cards.
The ramifications of web3 are practically irreversible owing to the immutable nature of blockchain. Furthermore, breaches in web3 platforms could mean that thousands of users could lose their digital assets permanently. Web3 security breaches could also damage the reputation of web3 platforms, which could last for an extended period.
The web3 cybersecurity infrastructure has a long way to go, as most of the web3 solutions rely on single-layer security solutions. As a matter of fact, the total losses from web3 security breaches in the first half of 2023 amounted to $655.61 million. Around 108 attacks have led to losses of almost $471 million. In 2022, the losses due to web3 security breaches amounted to almost $3.6 billion.
Definition of Web3 Security
The problems with web3 security and the massive scale of losses due to web3 security breaches have created curiosity about special measures for safeguarding your digital assets. The answers to ‘What is web3 security?’ point to the different processes, systems, and methodologies implemented for safeguarding decentralized technologies. Web3 security envisions protection of blockchain-based platforms, decentralized apps, and the digital assets of web3 users.
The distributed model used in web3 provides freedom from intermediaries, which improves privacy and transparency. However, the transparency exposes web3 to different types of threats. As the popularity of DeFi and NFTs continues growing, it is important to look for strong security measures to safeguard web3 solutions. You can safeguard your digital assets in web3 with a clear understanding of security and privacy risks.
Want to explore an in-depth understanding of security threats in DeFi projects? Enroll now in DeFi Security Fundamentals Course
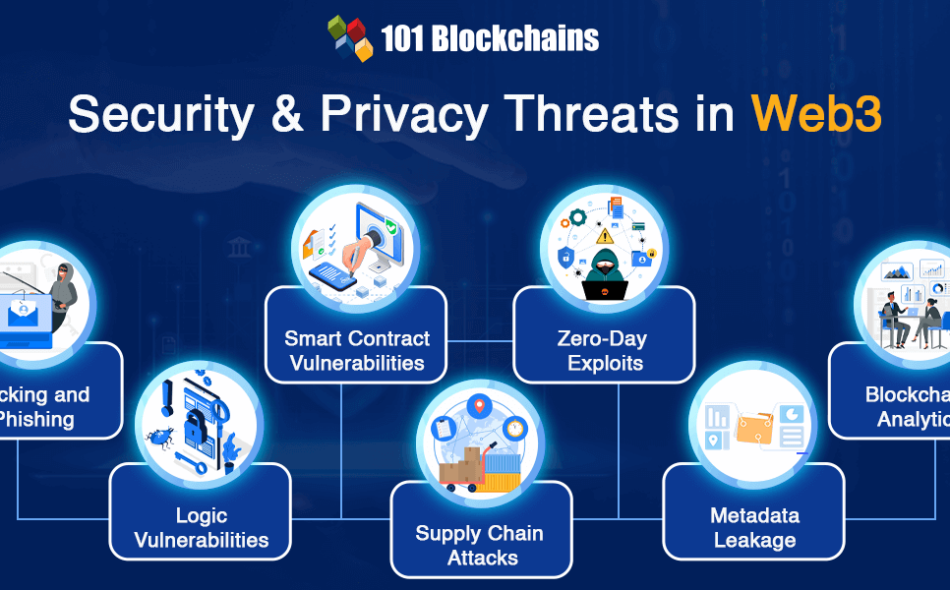
What are the Notable Security and Privacy Threats in Web3?
The ideal approach to staying safe against a problem is to understand the problem and the associated risks. With a comprehensive understanding of web3 security risks, you can find the best practices for resolving the threats. The risks for web3 users can be classified into security and privacy risks. Let us learn more about the common security and privacy risks you can find in web3.
-
Hacking and Phishing
The two popular web2 attacks which find their way into discussions about web3 security include hacking and phishing. Any web3 security guide would be incomplete without mentioning hacking and phishing attacks. Hackers could exploit the vulnerabilities in the dApp code logic or decentralized infrastructure to obtain unauthorized access to private keys, user wallets, and sensitive data.
Phishing attacks work by deceiving users so that they can reveal their private keys or any sensitive information. Phishing is one of the proven and effective approaches that hackers use to gain vital information from users. It is important to note that hackers could use social engineering skills for phishing attacks without relying on technical knowledge.
-
Smart Contract Vulnerabilities
Web3 security depends directly on security of smart contracts as they are the core components of the web3 ecosystem. Any individual who wants to learn web3 security best practices must familiarize themselves with smart contracts and how they work. Smart contracts work as automated agreements or transactions that could run independently upon satisfying certain conditions. Flaws in the smart contract could lead to unimaginable outcomes, such as unintended actions and loss of funds.
Excited to learn about the critical vulnerabilities and security risks in smart contract development, Enroll now in the Smart Contracts Security Course
-
Logic Vulnerabilities
Decentralized applications, or dApps, are also a core element of the web3 ecosystem and could lead to different security risks. dApps feature different types of vulnerabilities, including backdoors and logic vulnerabilities that could open the doors for hackers to exploit the contracts.
-
Supply Chain Attacks
Another noticeable type of attack in web3 refers to supply chain attacks in which attackers exploit a specific component of the web3 application. For example, attackers could exploit an open-source library implemented in the code of a web3 application.
-
Zero-Day Exploits
Zero-day exploits also affect security in web3 by exposing a vulnerability within the web3 community. It capitalizes on the lack of awareness about a specific vulnerability. Attackers could capitalize on such vulnerabilities to obtain unauthorized access to systems, deploy malware, or steal data.
-
Metadata Leakage
Web3 users must also pay attention to privacy risks such as metadata leakage. Metadata refers to the data that could expose important information about user transactions, such as sender and recipient addresses. You might wonder about the problems with metadata for web3 cybersecurity with the immutability of blockchain. It is true that no one can modify the transaction data on blockchain. However, malicious agents can use the metadata of a transaction to draw inferences about sensitive information of users.
-
Blockchain Analytics
The problems for web3 security also emerge from the innovative advancements in the web3 ecosystem. Blockchain analytics utilizes data analytics techniques for tracing the transaction flow on blockchain. It can serve promising outcomes for personalization of services for web3 users.
On the other hand, blockchain analytics could also expose sensitive information about users, including the identity of the user and amount of transactions. The possibilities of metadata leakage complement the risks associated with blockchain analytics by risking exposure to sensitive data.
Best Practices for Safeguarding Your Assets in Web3
The list of security risks in web3 is significantly extensive, and new types of security risks emerge every day. At the same time, the growing adoption of web3 also makes it a promising target for attackers. Cryptocurrencies, NFTs, virtual real estate, and many other assets are making their way into web3, which improves the value of assets locked in the web3 landscape. Here are some of the best practices you should follow for securing your assets in web3.
-
Utilize Hardware Wallets
The biggest risk in web3 is the threat of private key theft. Private keys help you gain control over your cryptocurrency and digital assets in web3. The best approach for securing digital assets is to prevent anyone from accessing your private keys. Interestingly, you can rely on a hardware wallet for storing your cryptocurrencies and digital assets with security. Hardware wallets store your private keys in offline storage with physical devices. Popular examples of hardware wallets include Trevor and Ledger. You can also utilize the hardware wallets as an additional layer for Metamask.
-
Practice Caution with the Recovery Phrase
The recovery phrase or seed phrase is another crucial piece of information that you should safeguard at all costs. The seed phrase includes a combination of 12 to 24 words, which can help in recovering your private keys. You can find references to safeguards for the seed phrase in responses to “What is web3 security?” as one of the common suggestions for web3 security. Remember that you should never share your recovery phrase with anyone or store it online. You can write down the recovery phrase on a piece of paper and store it in a secure location that only you can access.
-
Utilize Two-Factor Authentication
Another proven recommendation for safeguarding your digital assets in web3 is two-factor authentication. You can learn web3 security only by following some of the conventional tenets in web2 cybersecurity. Two-factor authentication has served as an effective layer of security for web2 applications, and it could work in the same way for web3.
The second factor implies that you would receive a code on your phone or one generated by an authentication app. Two-factor authentication could help in preventing unauthorized access when someone has compromised your password. Majority of web3 applications provide the facility of two-factor authentication, and users should always enable it in all cases.
Curious to develop an in-depth understanding of web3 application architecture? Enroll now in the Web3 Application Development Course
How Can You Choose the Right Tools for Securing Your Digital Assets?
Web3 users have to take responsibility for securing digital assets in their web3 experience. Therefore, it is important to select the right tools that could protect your digital assets against security threats. You can rely on effective web3 security software to avoid unwarranted compromises of your digital assets. Here are some of the features you should look for in a tool for securing web3 assets.
First of all, you must choose web3 security software with real-time protection. The software must provide real-time transaction audits to identify risky logic alongside critical vulnerabilities. In addition, it must also have a highly responsive notification or reporting mechanism for warning users.
Another important requirement for security in web3 would point to anti-phishing features. Phishing is a major security risk in web3, and anti-phishing features help in easier detection of phishing websites. It could help in blocking malicious websites and safeguarding your valuable assets.
Most important of all, the web3 security software must receive regular updates to identify latest threats. Updates are an important requirement for ensuring effective safeguards against emerging threats to web3 security.
Start your journey to becoming an expert in Web3 security skills with the guidance of industry experts through Web3 Security Expert Career Path
Conclusion
The best practices for safeguarding your digital assets in web3 would focus on preventing any vulnerabilities in smart contract code. In addition, users must also understand the implications of different web3 security risks and their origins. Web3 is a rapidly growing industry with the introduction of innovative solutions like NFTs, metaverse, and web3 games. The high value of assets in web3 has turned web3 into a hunting ground for malicious actors.
On top of it, the lucrative propositions for quick profits in web3 could deceive users into giving up sensitive information. Therefore, it is important to learn about web3 security and the best practices for protecting your assets. Familiarize yourself with the fundamentals of web3 and identify how you can ensure the best security for your web3 assets.
*Disclaimer: The article should not be taken as, and is not intended to provide any investment advice. Claims made in this article do not constitute investment advice and should not be taken as such. 101 Blockchains shall not be responsible for any loss sustained by any person who relies on this article. Do your own research!
The post Web3 Security: Safeguarding Your Digital Assets appeared first on 101 Blockchains.