The web3 ecosystem has been developing at a radical pace with new solutions and innovative advancements. At the same time, the complexity of smart contracts and DeFi protocols has also been growing at an unprecedented rate. Therefore, a web3 security audit is a mandatory requirement for ensuring security of user funds alongside maintaining trust in the web3 ecosystem.
For example, DEUS, a web3 protocol, became the victim of an attack on its recently launched stablecoin, DEI. Upon hiring a professional security audit firm, DEUS discovered that the attack had exploited a public burn vulnerability in the protocol. The losses for the protocol on Binance Smart Chain amounted to $1.3 million and exceeded $5 million on Arbitrum. It is important to recognize how a security audit before deploying the stablecoin might have saved DEUS from the losses.
Web3 represents a new version of the internet, which is decentralized and offers complete control and ownership over data and transactions. The major elements that build web3 include decentralization, implicit trust, and consensus mechanisms. You might wonder about the relevance of questions like “What is web3 auditing?” for a sector that is growing consistently with new developments.
As the web3 ecosystem grows bigger, it also brings the possibility of security risks. Since web3 apps are based on smart contracts deployed on blockchain networks, it is important to pay attention to their design and functionality. Web3 audits primarily focus on smart contract audits. Let us learn more about the importance and best practices to strengthen web3 security.
What are the Security Risks in Web3?
The first question on your mind before learning about security audits in web3 would point to security risks in web3. For starters, it is more secure than web2 owing to some fundamental principles. However, web3 security issues emerge from different factors, including the approaches for interaction between web3 and web2 architectures.
On the other hand, some security issues could emerge from functionalities of blockchain, smart contracts, IPFS, and other web3 components. Furthermore, web3 depends on network consensus, thereby creating challenges for resolving the flaws within time. Here is an outline of the most popular security risks in the domain of web3.
-
No Encryption and Verification for API Queries
Web3 applications have to depend on API queries and responses, which do not guarantee the authentication of connection endpoints. It is important to understand that web3 is completely decentralized, and the front-ends are still dependent on web2 technologies to ensure easier interaction for user endpoints. Since majority of web3 API queries do not have cryptographic signatures, they are vulnerable to data interception, on-path attacks, and many other security risks.
-
Privacy Lapses in Decentralized Storage Systems
The most distinctive trait of web3 is decentralization, which means that any connected node can store and access data on blockchain. You must recognize the importance of web3 security audit to resolve the multiple privacy and security concerns depending on the nature of data stored in decentralized storage systems. Research has proved that complete anonymity of data is a myth.
-
Smart Contract Vulnerabilities
The biggest threat to web3 security emerges in the form of smart contract vulnerabilities. Smart contracts are the core components of web3 as they help in automation of transaction and verification processes. For example, smart contracts can help in creating a trustworthy Automated Market Maker to facilitate transactions on a crypto exchange without waiting for other buyers or sellers. However, a web3 security audit checklist would revolve only around comprehensive and effective audits of smart contracts. In May 2022, Terra USD lost almost $50 billion to a smart contract vulnerability.
Excited to learn about the critical vulnerabilities and security risks in smart contract development, Enroll now in the Smart Contracts Security Course
Importance of Web3 Security Audits
The popular web3 security risks show that security issues in web3 could lead to overwhelming challenges for web3 adoption. Why would businesses trust web3 solutions when they lose millions to web3 security risks? On the other hand, best practices of web3 security audit could help in identifying the security issues before they cause any damage. Web3 has the potential to deliver the ‘next internet’ with more power to users. However, web3 security risks can create disruptions for businesses and users embracing web3 solutions.
The most noticeable ways in which web3 is being used by businesses include decentralized apps and DeFi. In addition, decentralized storage systems have also emerged as promising use cases of web3 for businesses. Considering the value of blockchain, smart contracts, dApps, and DeFi solutions, it is important to take the initiative to protect web3 solutions against security risks. Security audits not only help in identifying potential vulnerabilities or errors but also support the faster resolution of security issues.
Want to explore an in-depth understanding of security threats in DeFi projects? Enroll now in DeFi Security Fundamentals Course
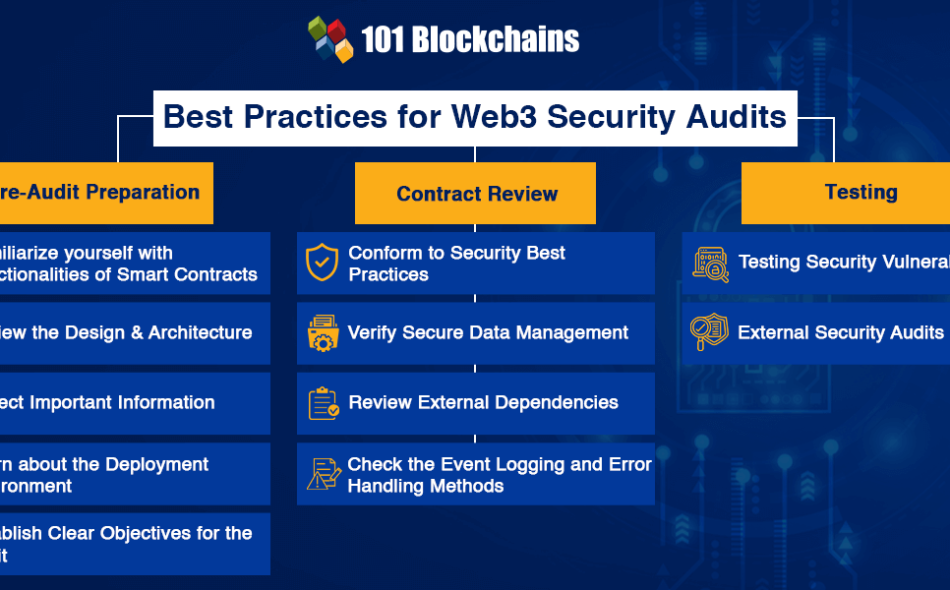
Best Practices for Web3 Security Audits
You might wonder about the answers to “What is web3 auditing?” before diving into the best practices. Web3 auditing refers to the combination of processes implemented for checking a web3 system or app before deployment. Interestingly, you cannot finish the security audit for web3 within one step.
At the same time, you must follow certain precautions and recommendations for obtaining the desired functionalities without security vulnerabilities. The best practices help in minimizing the risks with smart contracts alongside improving the security of web3 applications. Let us go through a review of best practices for web3 auditing across different stages of the audit process.
Pre-Audit Preparation
Before you start a web3 audit, it is important to go through a web3 security audit example and follow the best practices based on your inferences. The pre-audit preparation is essential for ensuring an efficient and smooth audit process. Here are some of the notable best practices involved in the preparation stage before the audit.
-
Familiarize yourself with Functionalities of Smart Contracts
First of all, you should understand the functionality of the smart contract and its purpose alongside the desired use cases. You should go through a comprehensive review of the specifications, documentation, and requirements of the smart contract. It can help you find an in-depth understanding of the intended behavior of a web3 solution.
-
Review the Design and Architecture
The next step in a web3 security audit would focus on a comprehensive review of the design and architecture of smart contracts powering a web3 solution. It can help you identify potential vulnerabilities and design flaws in the smart contract for a web3 application.
You should pay attention to factors such as access control mechanisms, contract structure, data flow, and contract interactions. It is also important to review the design of a smart contract according to the established standards, design patterns, and best practices.
Curious to develop an in-depth understanding of web3 application architecture? Enroll now in the Web3 Application Development Course
-
Collect Important Information
The web3 auditing process also involves collection of relevant information about the smart contract. Examples of essential information required for a web3 security audit checklist include the ABI of a contract, its source code, contract address, and the compiled bytecode. The ABI serves as a critical resource for facilitating interactions between the web3 application and smart contract.
-
Learn about the Deployment Environment
You can improve the web3 auditing process in the pre-audit preparation stage by understanding the deployment environment. The deployment environment of a web3 app would include the blockchain platform, relevant protocols, and preferred network for deployment. The review of deployment environment for a web3 application could help in identifying web3 security issues within the specific context. You should learn about the important technical details as well as the limitations in the deployment environment.
-
Establish Clear Objectives for the Audit
One of the most important best practices for web3 auditing is establishing a clear set of objectives. Web3 audits without clearly defined scopes are more likely to end up with misguided initiatives. On the other hand, the best practices of web3 security audit emphasize the necessity of defining a scope for the web3 audit.
The scope would outline the specific functionalities, contracts, and areas of the web3 application that should be subject to audits. In addition, you must also define the objectives, timeline, and deliverables of the audit in collaboration with contract development team. It is also important to define the rules of engagement, reporting format, and communication channels.
Contract Review
The second stage in the web3 security audit process focuses on contract review, which is the most important part of the audit. The contract review provides a comprehensive review of the source code of the smart contract that powers the web3 application. With the comprehensive review, you can find possible vulnerabilities alongside ensuring an assessment of the overall security posture. Here are some of the most prominent best practices involved in the contract review for web3 applications.
-
Conform to Security Best Practices
It is important to comply with the established best practices for web3 security alongside following important guidelines for developing smart contracts. For example, you must follow the important security considerations for Solidity contracts. Any web3 security audit example would show how the security considerations of Solidity could help in identifying common security vulnerabilities, such as access control issues, reentrancy, and integer overflow or underflow.
-
Verify Secure Data Management
The web3 audit process must emphasize the security of data management. You should check how the smart contract manages sensitive data, including external dependencies, user data, and contract state variables. It is also important to check the contract for data sanitization, secure storage practices, and preventing data leakage.
-
Review External Dependencies
The importance of web3 security audit would also point toward the scope for reviewing external dependencies, like oracles, libraries, and APIs. It is important to ensure that all the dependencies are secure, updated, and audited to mitigate potential exploits or vulnerabilities.
You should also verify the interactions of smart contracts with external contracts and check the validation and authentication of external contracts. On top of it, the audit must check that the contract also leverages secure mechanisms for facilitating easier interactions.
-
Check the Event Logging and Error Handling Methods
Another crucial best practice for web3 audit in the contract review stage reflects on checking the methods for event logging and error handling. Auditors should follow an ideal web3 security audit checklist for checking whether the web3 app has logged events with the details required for debugging and auditing. In addition, auditors should also check for robust error handling that can help in preventing unexpected vulnerabilities or errors.
Testing
The completion of the contract review stage leads you to another important stage in the web3 auditing process. You would have to implement in-depth tests for the smart contract to detect and resolve potential vulnerabilities. Here are the recommended best practices for smart contract testing for web3 auditing.
-
Testing Security Vulnerabilities
Auditors could follow the best practices of web3 security audit for testing security vulnerabilities with recognized tools. For example, you can find a broad range of testing tools, including MythX, Mythril, Slither, and others, which help in detecting smart contract security vulnerabilities.
It is important to remember that you need comprehensive testing that would cover different attack vectors and use case scenarios. Auditors must rely on the combination of manual and automated testing techniques for facilitating comprehensive coverage.
-
External Security Audits
The most important best practice for web3 audits would point toward selection of a professional external security audit firm. You should capitalize on the services of third-party security audit firms or auditors for conducting external security audits.
On top of it, external auditors would introduce a fresh perspective, guiding you with recommendations and insights for improving the security of smart contracts. The advantage of choosing professional audit firms for external security audits is the availability of detailed documentation and real-time reporting mechanisms.
Start your journey to becoming an expert in Web3 security with Web3 Security Expert Career Path
Final Words
The importance of security audits in web3, alongside the best practices for security audits, proves that audits are crucial for web3 security. Web3 encompasses a wide range of applications and technologies, including blockchain technology, dApps, and smart contracts. Interestingly, smart contracts serve as the focal element in a web3 security audit apart from the testing mechanisms, tools, and frameworks involved in audits.
At the same time, it is important to rely on the services of third-party auditors for an independent overview of the security status of the smart contract. As the web3 ecosystem grows bigger, security threats will have some major implications for adoption of web3. Learn more about web3 security and some of the prominent challenges to web3 security in detail now.
*Disclaimer: The article should not be taken as, and is not intended to provide any investment advice. Claims made in this article do not constitute investment advice and should not be taken as such. 101 Blockchains shall not be responsible for any loss sustained by any person who relies on this article. Do your own research!
The post Web3 Security Audit: Importance and Best Practices appeared first on 101 Blockchains.